Security Pattern – API Services
Overview
The following security pattern describes the security architecture for enabling applications exposing Restful API’s.
This pattern will focus on applications deployed as a microservices architecture. Microservices are built around decoupled components that are separated into individual self-contained applications and invoke each other across network communication services. Microservice applications represent small, loosely coupled entities that communicate with each other (typically) via RESTful interfaces over HTTPS.
This differs in comparison to traditional monolithic architectures, whereby each component invokes another using internalised methods via shared memory or system resources within the same host.
The document focuses on the challenges associated with establishing a microservices architecture and the typical methods of deployment.
Typical Challenges
- Tracking, managing and enforcing access controls for APIs that expose data held in internal backend databases, repositories and data storage.
- The decoupled nature of microservice applications increases the risk of inadvertently exposing internal functionality and components. Threats can target weaknesses within those microservices by directly communicating across exposed API interfaces on the network.
- API-based microservices typically form a broader ecosystem of interactions for multiple consumers. API endpoints exposed may be consumed by a blend of internal, public or partner API clients with different security postures. These models also break down traditional perimeter-based network segregation (DMZ) for securing web application services.
- Microservices architecture allows for faster and more agile development cycles, but subsequently can allow for broader logic flaws to occur due to the additional complexity of managing distributed systems.
Scope
The scope of this document is to address the security threats that relate to
| ID | Description | Example |
|---|---|---|
| 01 | Deployment and execution of restful API-based Service | Node.js microservice application |
| 02 | Consumption of API Service from internal and external clients | External B2B (Partner) and B2C (Consumer) clients |
Out of Scope
| ID | Description of exclusion | Reason for Exclusion |
|---|---|---|
| 01 | This pattern does not cover SOAP-based services, XML-structured communications or web sockets. | These services require additional considerations to threat modelling and web app security. |
| 02 | Application development environments and tooling | Covered under broader security patterns such as Source Code Management and CI/CD Pipelines. |
Dependencies
| ID | Description | Impact from dependency not met |
|---|---|---|
| 01 | The listed cybersecurity security principles and controls have been referenced from ASCS ISM December 2022 release | Requires update to match latest published ISM. |
Assumptions
| ID | Description | Impact if assumption is false |
|---|---|---|
| 01 | Design decisions assume API Service conforms to standard practices in Restful API design. | Non-conformance to best practise for Restful API will require separate considerations to controls. |
| 02 | Design decisions assume API Service is deployed as an autonomous web application (such as a microservice). | Different threat modelling is required for other platform hosting and orchestration services. |
Assets at Risk
The following section provides a list of assets affected by the problem statement:
| Asset Title | Asset Description |
|---|---|
| API Service | Represents a web application that exposes one or more APIs (Application Programming Interface) that provide a set of operations for consuming, processing or transforming data. |
| API Gateway | Primary function of the API gateway is to route inbound API requests to the correct API Service. It can be used as a front-door and enforcement point when exposing API to various consumers (such as external, partners and or internal developers). |
| API Lifecycle Manager | Allow developers to register, publish, promote and manage API Services exposed via the API Gateway. This includes developer portals for searching and discovering published API’s associated with specific API Service. This also typically integrates into CI/CD tooling used for deployments. |
The following assets are also referenced within the pattern but not in scope
- Identity Provider – Referenced in this pattern to describe services used to authenticate clients.
- Secure Token Service – Referenced in this pattern to describe services used for issuing access tokens for authentication and authorisation.
- CI/CD tooling – Required to deploy API Service into target hosting platform and environments.
Threat Model
The following section provides a list of threats within the problem statement:
| Threat Event (ID / Title) | Threat Description and Characteristics | Diagram |
|---|---|---|
| TE-14: Inadequate workflows or processes leading to flaws in deployment | Microservice-based web applications have increased exposure to flaws in workflows and processes due to their distributed nature. Security controls implemented for upstream components could be skipped or bypassed by directly accessing downstream components (confused deputy scenario). A microservice may be restricted from accessing sensitive processes, data or information but can still gain access by forwarding requests via other intermediary or downstream microservices with approved access. | 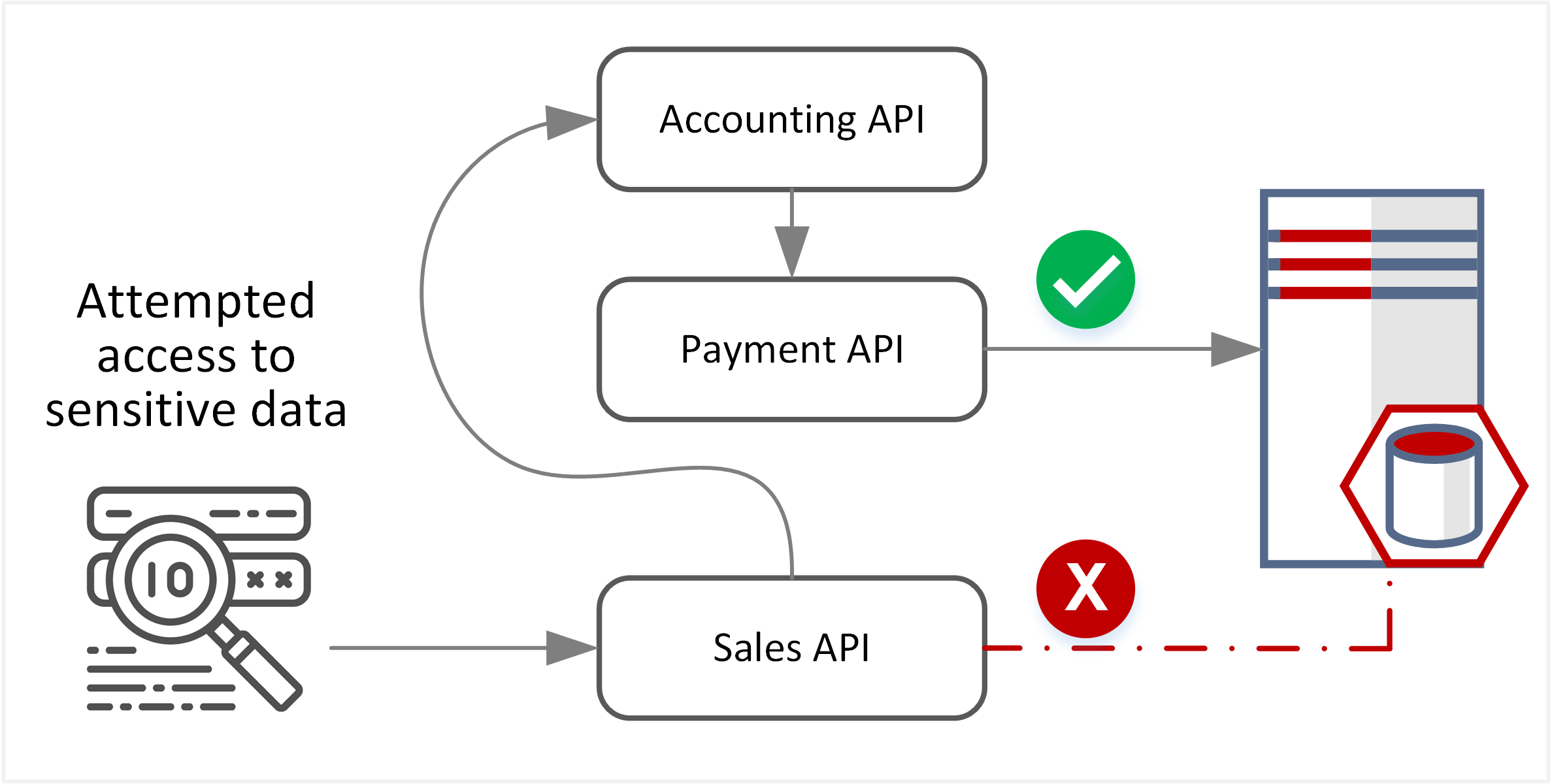 |
| TE-24: Identity theft or impersonation | API Services rely on passing identity and context within each request to communicate with other API Service or backend data services. This opens up exposure to replay attacks for tokens, thief of exposed tokens/API Keys in query strings or exposure of unprotected credentials within HTTP header requests. | 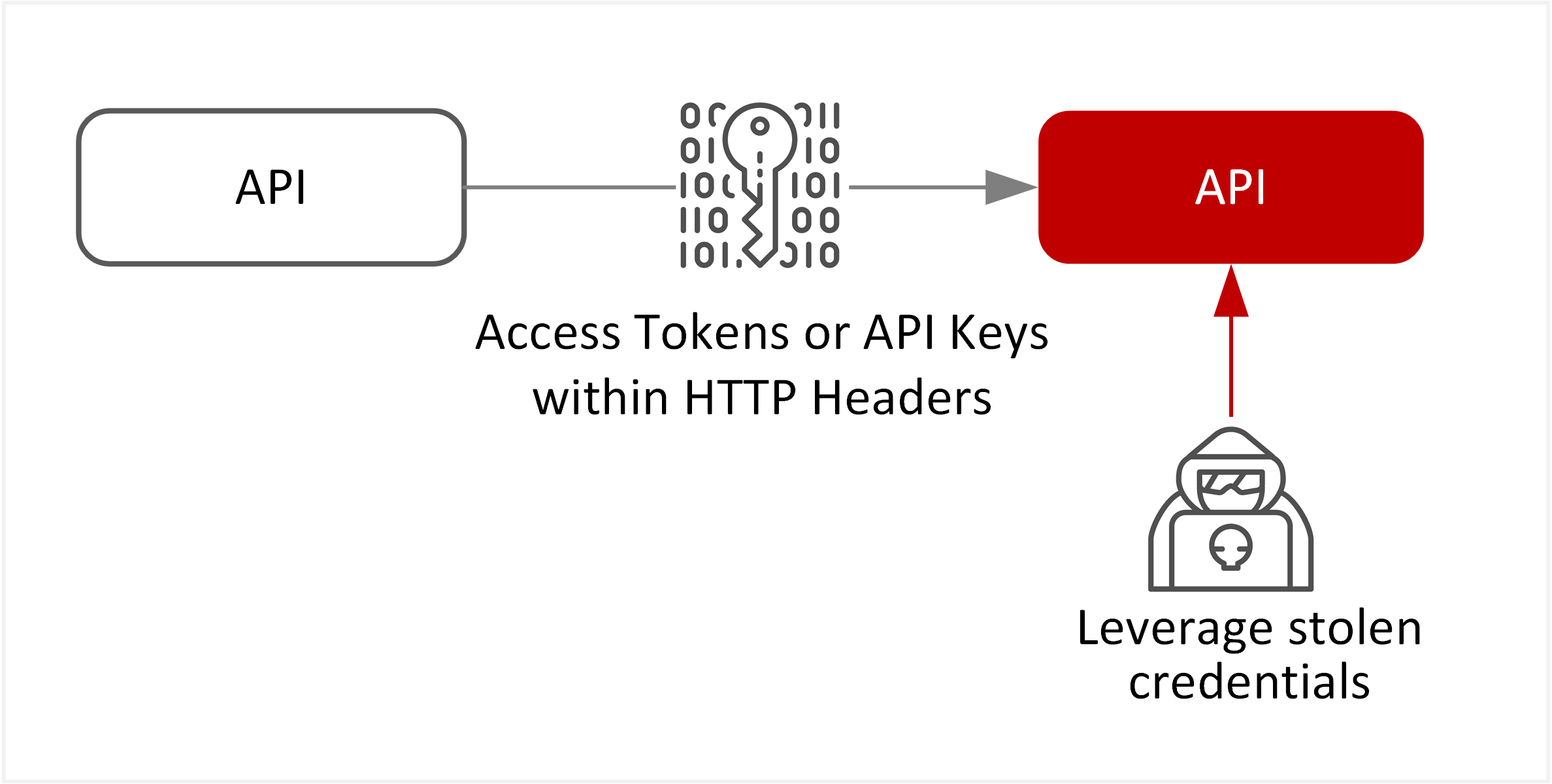 |
| TE-26: Abuse of resources through misconfiguration | Web applications exposing API services are vulnerable to application flaws, misconfiguration for backend data flows or misconfiguration of TLS settings. The API Service could be compromised if these flaws are exploited or data is unintentionally exposure |  |
| TE-29: Web application attacks or code injection attack | Web applications exposing API services remain vulnerable to web application attacks and susceptible to command injection, encoding or serialisation attacks, cross-site scripting (XSS), Cross-Site Request Forgery (CSRF), and HTTP parameter tampering. | 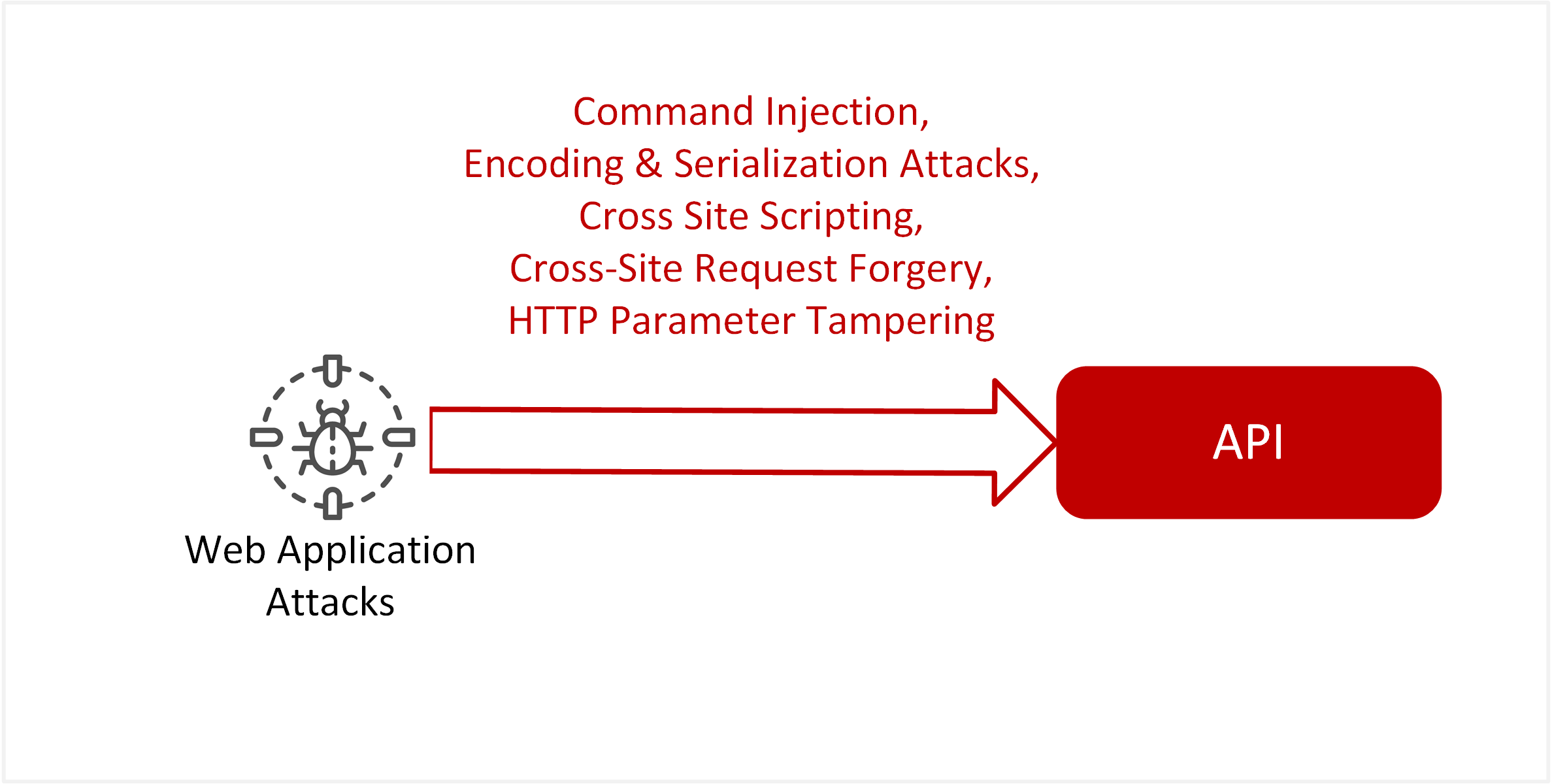 |
| TE-40: Distributed Denial of service (DDoS) across application services | Denial of service attackers may overwhelm web applications with a flood of HTTP/HTTPS requests. Flaws in processing or load balancing of HTTP traffic may also allow for an application-based DOS attack. | 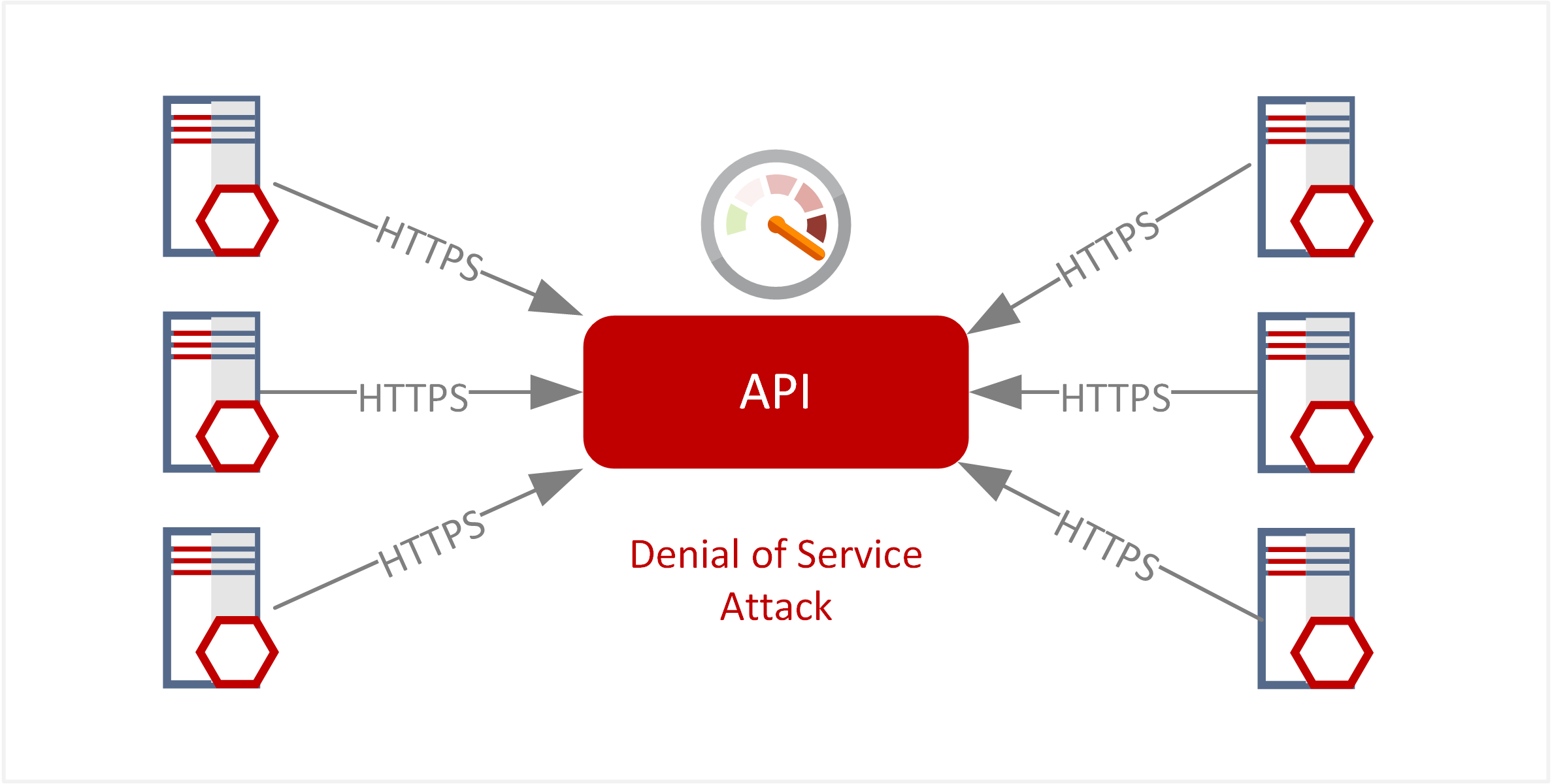 |
Target State Solution
Summary
The target state solution evaluates the following design requirements to provide the expected target state solution and design principles.
Design Requirements
The target state solution is required to meet the following requirements, as referenced under Dependencies, Assumptions and Constraints.
| Requirement | Implication to Design Principles |
|---|---|
| 1. The scope and level of protection are specific and appropriate to the asset at risk. | Maintain segregation of API Services for connectivity between security domains and environments |
| 2. Security mechanisms must be pervasive, simple, scalable, and easy to manage. | The security pattern maintains clear security principles to be applied for API Services |
| 3. Assume context at your peril. | Controls defined in this security pattern is used to identify and measure problems, limitations or issues |
| 4. Devices and applications must communicate using open, secure protocols. | Open and encrypted communication channels such as HTTPS are applied for API Services |
| 5. All devices must be capable of maintaining their security policy on an un-trusted network. | API Services are protected against both external and internal threats |
| 6. All people, processes, and technology must have declared and transparent levels of trust for any transaction to take place. | Validate and inspect all traffic flows to API Services via API Gateways |
| 7. Mutual trust assurance levels must be determinable. | Apply mutual trust between API Gateway and API Services |
| 8. Authentication, authorisation, and accountability must interoperate/exchange outside your locus/area of control. | Apply authentication and authorisation for internal, partner and public clients. |
| 9. Access to data is controlled by security attributes of the data itself. | Maintain security attributes for API Services |
| 10. Data privacy (and security of any asset of sufficiently high value) requires a segregation of duties/privileges. | Apply access restrictions to API Service for environments hosting sensitive or high value data |
| 11. By default, data must be appropriately secured when stored, in transit, and in use. | Apply uniform security policies within API Gateway for inbound, outbound and mediated traffic flows for API Services |
Solution Overview
The enforcement of segmentation for API Services is reliant on API Gateway. API Services establish mutual trust with API Gateway to allow delegation to enforce security controls. This includes maintaining segregation for flows between environments and different flows.
The consumption of API Services can be summarised into three main interactions. These interactions are separated into inbound, outbound and internal flows across trust boundaries.
| Flow Direction | Description |
|---|---|
| Inbound Flows | These flows represent various clients consuming API Services using the API Gateway as a broker. |
| Outbound Flows | These flows represent API Service consuming other internal or external services. |
| Internal Flows | These flows represent API Service consuming other API Services exposed using the API Gateway as a broker. |
These interactions have different implications for how security controls are applied. The following further describes the security model for each flow.
Inbound Flows
The following diagram represents inbound flows from different client types to API Services.

Regardless of location (internal, public or partner) all inbound flows from various client types are strongly authenticated. The below summary list of client types is expected to authenticate using the following industry standards.
| Client Type | Example | Recommended methods [1] |
|---|---|---|
| Browser | Internet browser executing Single Page Application (SPA) on a client machine. e.g. Chrome or Firefox | OpenID Connect Authorisation Code Type OR OpenID Connect Implicit Grant Type |
| Application Client | Stand-alone application that runs on a client machine, i.e.: .NET or Java application running on a workstation. | OpenID Connect Authorisation Code Type. |
| Native | Stand-alone application that runs on a mobile device, e.g. iOS or Android. | OpenID Connect Authorisation Code Type. |
| System to System | System application runs on a server machine to consume APIs e.g. Partner B2B transactions | OAuth2 Client Credentials grant over TLS-MA. |
| Server-Side Application | Traditional frontend web application that runs on a server machine to consume backend APIs. | N/A – Specific authentication method implemented on frontend presentation server, not in scope for this pattern. |
[1] Note: The following is a summary based on industry best practices at the time of writing. Please also refer to the latest documentation from OpenID Connect and OAuth standards regarding best practices for authentication and authorisation for specific implementations.
Outbound Flows
The following diagram represents outbound flows from API Service to a service provider.
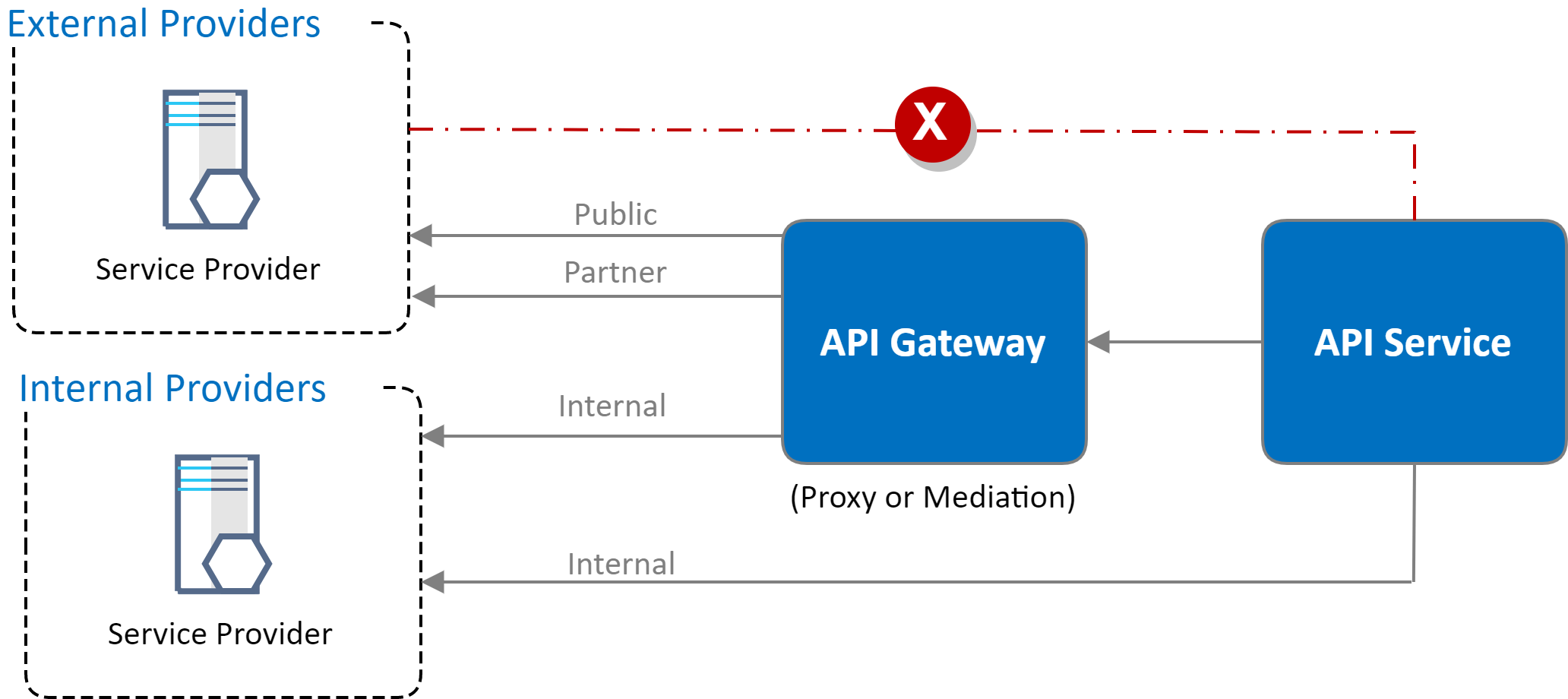
Additional Notes
- Any traffic to external public or partner locations uses content inspection for protection against data exfiltration.
- Some controls may look to allowlist connectivity to partners where controls are not applicable (e.g. web content filtering)
- API Service traffic to backend internal provider services is not required to traverse the API Gateway (as enforcement and access control are maintained within those assets).
- Connectivity may traverse the API Gateway if mediation is required (e.g. Converting RESTful-based JSON formatted traffic into SOAP-based XML traffic).
Internal Flows
The following diagram represents internal flows originating from API Service to another API Service.
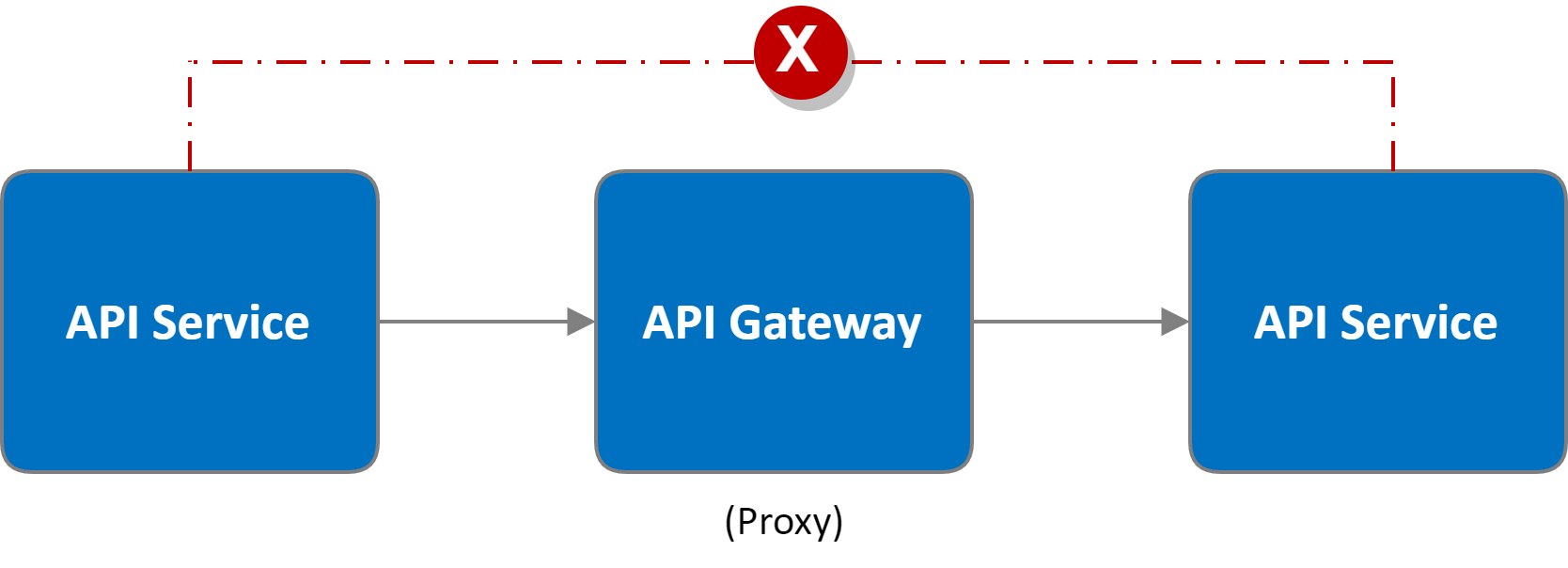
Additional Notes
- API Service to API Service communications occurs via API Gateway as an intermediary proxy.
- The API Gateway is responsible for maintaining boundaries between API Services.
Design Principles
The following design principles are applied for this pattern based on the requirements.
- API Gateway is an enforcement point for inbound, outbound and internal flows.
- API Gateway enforces flow segregation between Development, Non-Production and Production environments.
- Apply ‘shift-left’ methodology for security controls in Non-Production and Pre-Production environments.
- Maintain segmentation between API Services using controls within both network security and identity and access management.
- API Services are deployed as immutable services within environments.
Actors
List the actors involved in this pattern.
| Actor Type | Actor Description |
|---|---|
| Internal API consumers | Internal staff consuming API Services typically via native or browser client types |
| Public API consumers (B2C) | External public consumer or anonymous access to API Services |
| Partner API consumers (B2B) | External partners or supplier access to API Services |
| API Developers | Application developers for building, compiling and deploying API Services. |
| System Administrators | Manage and operate API Gateway and API Lifecycle tooling. |
Locations
This pattern is applied to any locations for assets being utilised.
| Location | Location Description |
|---|---|
| Application Development Environment | Development or sandpit environment for API development |
| Application Test Environment | Non-production and pre-production environment for API testing and release |
| Application Production Environment | Production environment for deploying and publishing APIs that have passed all testing stage gates |
Sequencing
The pattern is designed within the following sequences.
| Stage gate | Description |
|---|---|
| Build time | Development and Build stage gate for API Services |
| Deploy time | Deploy and release stage gates for API Services |
| Run time | Execution stage gate for API Services |
Mapping Threats to Controls
The following provides a mapping of security threats to affected assets and the security control objectives required to mitigate them (further detailed in subsequent security pattern logical designs).
| Threat Event | Affects Assets | Security Controls Objectives |
|---|---|---|
| TE-14: Inadequate workflows or processes leading to flaws in deployment | API Service
API Lifecycle Manager |
ISM-0289: Installation and configuration of evaluated products
ISM-0400: Development, testing and production environments ISM-0402: Application testing and maintenance ISM-0469: Encrypting data in transit ISM-0616: System administrators for gateways ISM-1182: Network access controls ISM-1420: Development, testing and production environments ISM-1436: Segregation of critical online services ISM-1780: Secure software design and development |
| TE-24: Identity theft or impersonation | API Service
API Gateway |
ISM-0120: Access to sufficient data sources and tools
ISM-0469: Encrypting data in transit ISM-0634: Gateway event logging and alerting ISM-1424: Web browser-based controls ISM-1536: Web application event logging ISM-1546: Authenticating to systems ISM-1757: Web application event logging ISM-1775: Gateway event logging and alerting ISM-1817: Web application programming interfaces ISM-1818: Web application programming interfaces |
| TE-26: Abuse of resources through misconfiguration | API Service
API Gateway |
ISM-0289: Installation and configuration of evaluated products
ISM-0628: Implementing gateways ISM-0634: Gateway event logging and alerting ISM-1037: Assessment of gateways ISM-1536: Web application event logging ISM-1757: Web application event logging ISM-1775: Gateway event logging and alerting ISM-1780: Secure software design and development |
| TE-29: Web application attacks or code injection attack | API Service | ISM-0634: Gateway event logging and alerting
ISM-0649: Allowing specific content types ISM-0649: Allowing specific content types ISM-1240: Web application input handling ISM-1241: Web application output encoding ISM-1284: Content validation ISM-1284: Content validation ISM-1436: Segregation of critical online services ISM-1536: Web application event logging ISM-1757: Web application event logging ISM-1775: Gateway event logging and alerting |
| TE-40: Distributed Denial of service (DDoS) across application services | API Gateway | ISM-0971: Open Web Application Security Project
ISM-1431: Denial of service strategies ISM-1435: Monitoring with real-time alerting for online services ISM-1579: Availability planning and monitoring for online services |
Security Pattern
Pattern View: API Services
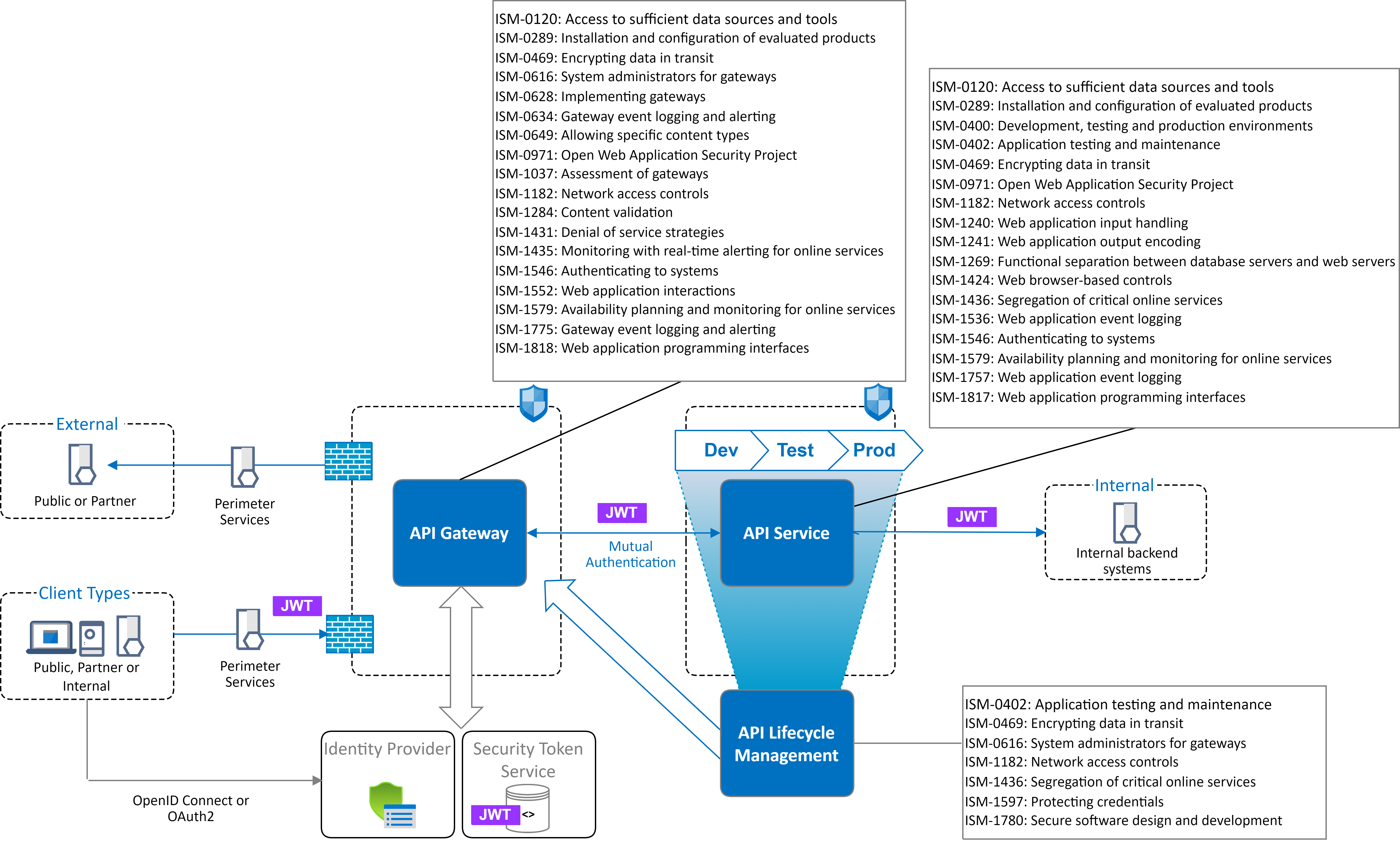
Control list: API Service
| Control Objective | Control Description |
|---|---|
| ISM-0120: Access to sufficient data sources and tools | Monitor for indicators of compromise across API services, including use of honeypot API services for the detection of malicious activity or use of compromised credentials. |
| ISM-0289: Installation and configuration of evaluated products | Maintain hardened security configuration for exposing API Service in accordance with vendor guidance and evaluation documentation. |
| ISM-0400: Development, testing and production environments | API Service deployments are partitioned and segregated between environments (Production, Testing and Development). |
| ISM-0402: Application testing and maintenance | Regularly apply vulnerability scanning across API interfaces to identify potential weaknesses or web application flaws or misconfiguration before release. |
| ISM-0469: Encrypting data in transit | Enforce secure ASD-Approved Cryptographic (AACP) protocols or high-assurance cryptographic protocols for data transmission. |
| ISM-0971: Open Web Application Security Project | Security testing is applied for API Services within Application Testing Environment, as prescribed by OWASP Application Security Verification Standard. This may include Static Source Code Analysis, Software Component Analysis, Malware Scan or Dynamic application security testing. |
| ISM-1182: Network access controls | Access controls are implemented to ensure hosted API services are consumed via the API Gateway. |
| ISM-1240: Web application input handling | Validation or sanitisation is performed on all input handled by the API Service. |
| ISM-1241: Web application output encoding | Output encoding is performed on all output produced by the API Service. |
| ISM-1269: Functional separation between database servers and web servers | Ensure separation between API Services and access to backend database systems. |
| ISM-1424: Web browser-based controls | Web applications implement Content-Security-Policy, HSTS and X-Frame-Options via security policy in response headers. |
| ISM-1436: Segregation of critical online services | Maintain metadata for each API Service regarding security categorisation and approved exposure across different endpoints (e.g. Internal, Partner and Public). |
| ISM-1536: Web application event logging | Hosted API Services must log security events that include: attempted access that is denied, crashes and error messages and API request headers (with any sensitive data, API Keys or Access Tokens being obfuscated). |
| ISM-1546: Authenticating to systems | Resource level access control for users is validated via the API Gateway. Fine-Grained User access is validated within API Service. Ensure users are authenticated prior to granting access API resources. Verify tokens or credentials are valid and issued from a trusted identity provider |
| ISM-1579: Availability planning and monitoring for online services | Apply performance counters, thresholds and rate limitation to protect the availability of APIs and backend resources. |
| ISM-1757: Web application event logging | API security events are aggregated into centralised security event monitoring (SIEM). |
| ISM-1817: Web application programming interfaces | Clients are authenticated when calling web APIs that facilitate access to data not authorised for release into the public domain. |
Control list: API Gateway
| Control Objective | Control Description |
|---|---|
| ISM-0120: Access to sufficient data sources and tools | Expose APIs as honeypot API Services to detect malicious behaviour, attempts to use stolen credentials or other indicators of compromise. |
| ISM-0289: Installation and configuration of evaluated products | Maintain hardened security configuration for API Gateways and exposed endpoints in accordance with vendor guidance and evaluation documentation. |
| ISM-0469: Encrypting data in transit | Enforce secure ASD-Approved Cryptographic (AACP) protocols or high-assurance cryptographic protocols for data transmission. |
| ISM-0616: System administrators for gateways | Uniquely identify all administrative access to API Gateway services and apply separation of duties to those performing administrative activities. |
| ISM-0628: Implementing gateways | Expose separate endpoints to API consumers that originate from different security domains (e.g. Internal, Partner, Public). Apply API firewall rules to control access to backend APIs. |
| ISM-0634: Gateway event logging and alerting | Endpoints exposed via API Gateways generate security authentication and authorisation audit records for all API transactions. This includes API Requests and data flows permitted through the gateway, API Requests and data flows blocked by the gateway, Real-time alerts for attempted intrusions. |
| ISM-0649: Allowing specific content types | Files uploaded or downloaded for APIs exposed via API gateways are filtered for allowed file types. |
| ISM-0971: Open Web Application Security Project | Enforce web application firewall rules to inspect API messages (e.g. CWE/SANS Top 25 or OWASP Top 10). Ensure API messages containing binary data or used for file transfer are scanned against malicious payloads or malware. |
| ISM-1037: Assessment of gateways | API Gateways undergo testing following configuration changes, and at regular intervals no more than six months apart, to validate they conform to expected security configurations. |
| ISM-1182: Network access controls | Ensure access controls for API requests are enforced via API Gateway to limit API traffic between endpoints to only those required for business purposes. |
| ISM-1284: Content validation | Files uploaded or downloaded for APIs exposed via API gateways undergo content validation. |
| ISM-1431: Denial of service strategies | Denial of Service and Distributed Denial of Service Protection is implemented for protection against network and HTTP protocol abuse. |
| ISM-1435: Monitoring with real-time alerting for online services | Apply performance counters, thresholds and rate limitation to protect the availability of APIs and backend resources. Enable real-time alerting to detect denial of service attacks and measure their impact. |
| ISM-1546: Authenticating to systems | Resource level access controls are validated within API Gateway, based on access tokens. Fine-Grained access controls are validated within API Service. Challenge clients for access credentials from trusted identity providers. |
| ISM-1552: Web application interactions | Endpoints exposed to different security domains using HTTPS, utilise a trusted Certificate Authority for that domain (e.g. Internal, Public) |
| ISM-1579: Availability planning and monitoring for online services | Support backend scaling of API Services to mitigate Denial of Service attacks. |
| ISM-1775: Gateway event logging and alerting | API Gateway event logs are aggregated into centralised security event monitoring (SIEM). |
| ISM-1818: Web application programming interfaces | Client access to APIs is authenticated and authorised using industry standards such as OpenID Connect or OAuth2. |
Control list: API Lifecycle
| Control Objective | Control Description |
|---|---|
| ISM-0402: Application testing and maintenance | Any API Service detected with security defects identified in test environments are not permitted onto further release phases into Production. |
| ISM-0469: Encrypting data in transit | Enforce secure ASD-Approved Cryptographic (AACP) protocols or high-assurance cryptographic protocols for data transmission. |
| ISM-0616: System administrators for gateways | Uniquely identify all users accessing API developer portals or API lifecycle tooling and apply separation of duties to those performing any administrative activities. |
| ISM-1182: Network access controls | Restrict access to system functions for API lifecycle management and API developer portals to only those required for business purposes. |
| ISM-1436: Segregation of critical online services | API lifecycle management portals capture security categorisations to ensure critical API services are segregated from other API services that are more likely to be targeted. |
| ISM-1597: Protecting credentials | Sensitive authentication data such as API keys, certificates or credentials are managed using a purpose-built security service such as secrets management. |
| ISM-1780: Secure software design and development | Ensure standard deployment and release of API Services across environments using approved DevSecOps tooling. |
Appendix A – References
Please see below links to external sites for further reading
- https://www.cyber.gov.au/acsc/view-all-content/ism
- https://microservices.io/patterns/microservices.html
- https://www.owasp.org/index.php/REST_Security_Cheat_Sheet
Appendix B - Disclosure Notice
This document is published as independent research only and is without warrenty. It does not represent any publication from Australian Cyber Security Centre (ACSC), the Australian Signals Directorate (ASD) or other associated Australian government entities.
