Introduction
This is a quick guide to writing a security pattern. For the full step-by-step guide, see the following link for How to Write a Security Pattern.
The guides and resources made available are intended for audiences with moderate background in security or architecture. Where-ever possible, I’ve also referenced additional external links for further reading.
Why Use Security Patterns ?
Security patterns are design artefacts that represent a defined and re-usable solution to a recurring security problems. The security patterns defined in these guides are asset-centric and focus describing security controls in context of those assets. Patterns ensure the security controls identified are based on threat modelling associated to protecting the assets.
There’s a lot of different initiatives that may trigger you to write a security pattern, such as
- Security risks or issues raised by a project team that require mitigation.
- Security concerns based on issues identified within similar organisations.
- New product or capabilities being brought into your organisation.
The guides made available in securitypatterns.io provide steps for both writing and using your own security patterns.

Feel free to customise this for your own purposes (and in fact, we encourage you to do so). Just make sure it maintains the following 4 characteristics.
- Context of a security problem and how it affects the asset.
- Abstracted from specific vendor or technology implementations.
- Maintains standards for threat and control taxonomies to promote reusability.
- Maintains traceability of prescribed controls to the original threats being mitigated.
How to Write a Security Pattern
The following quick guide provides a summary of steps for writing security patterns, based on the template made available under Resources.
Steps

| Task | Description |
|---|---|
| Identify the scope and typical challenges | First step is to define the scope of the security pattern to a single problem space and the typical challenges associated to security. Describe the problem in context of the assets affected by it. Reference any historic use cases or examples for the described problem. |
| Prepare and research | Collate research notes that will form the basis of your threat modelling and the solution. This will likely also form the initial view of the security principles and controls required in the pattern. |

| Task | Description |
|---|---|
| Identify the assets for the pattern | Identify and categorise the assets affected by the problem statement. Assets are considered autonomous or discrete sets of technology capabilities or components within a platform or system. Examples may include devices, applications, platforms, data storage or networks. |

| Task | Description |
|---|---|
| Establish Threat Modelling | Identify the Threat Event and Characteristics that affect the assets. Provide a description for each Security Threat, in context to the assets. Categorise each threat against the Threats Events Taxonomy. |
Reference: Threats Events Taxonomy

| Task | Description |
|---|---|
| Describe the target state solution | List out design requirements and their implication to the solution. Describe the target state solution, incorporate any requirements and describe the Security Principles. Consider the Actors, Locations and Sequences that influence the solution design. |
| Map threats to assets | Decompose threats and map to each asset. For each threat identify which assets are vulnerable to that threat. |
| Map controls to threats | For each threat identify the mitigating security controls. |
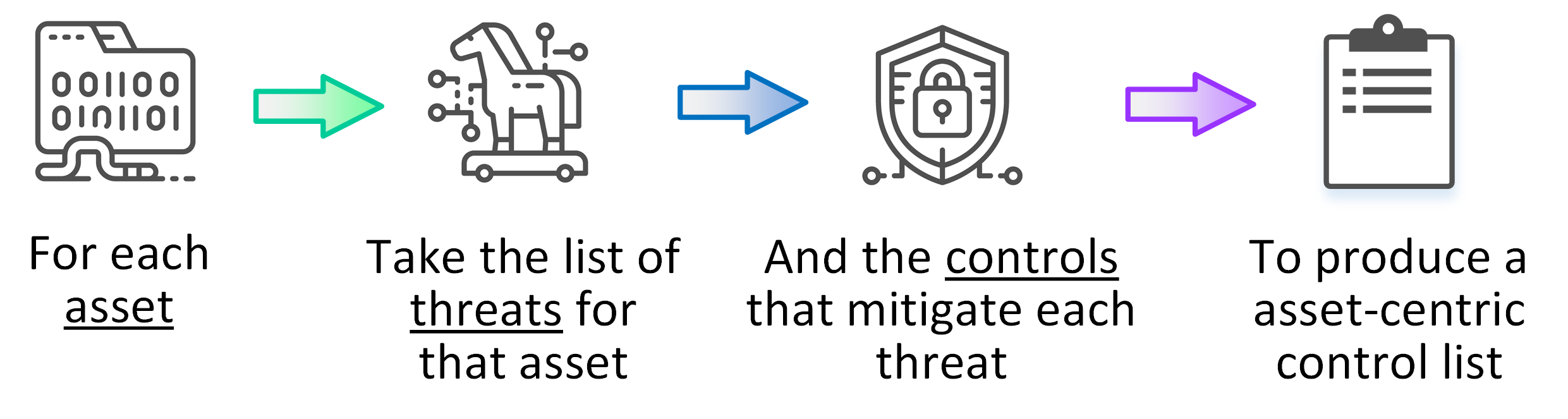
| Describe the security pattern | Collate and extract the security pattern for each asset, by combining the previous mappings for Threats, Assets and Controls. Build the asset-centric security pattern using the following 4 basic steps (shown in diagram below). Categorise each security control against the Security Controls Taxonomy and provide a description for each control, in context to the assets. |
Reference: Security Controls Taxonomy
Final Summary
That’s it !
To read through the full Step-by-Step Guide check out How to Write a Security Pattern or jump straight into reading How to Use a Security Pattern.
For working examples of security patterns, check out the following Security Patterns
About Us
The content on securitypatterns.io is provided as open material and free of charge under creative commons license.
